The Number One Security Challenge for Your Supply Chain Footprint in 2024
It’s no secret that cybersecurity threats are on the rise, and even tech giants li...

It’s no secret that cybersecurity threats are on the rise, and even tech giants li...

Very recent breaches at LastPass and Norton LifeLock have stirred up the debate ab...

Big news in, we have just released a major feature: Instant Shadow IT Discovery! T...

Phishing attacks need no introduction, so we will skip the part where we discuss h...
The recently released report by the National Cybersecurity Alliance on the percept...

When it comes to shadow IT and security, we have blogged about the oversight and c...

In the cutting-edge world of data, visibility into cloud and SaaS usage has been o...
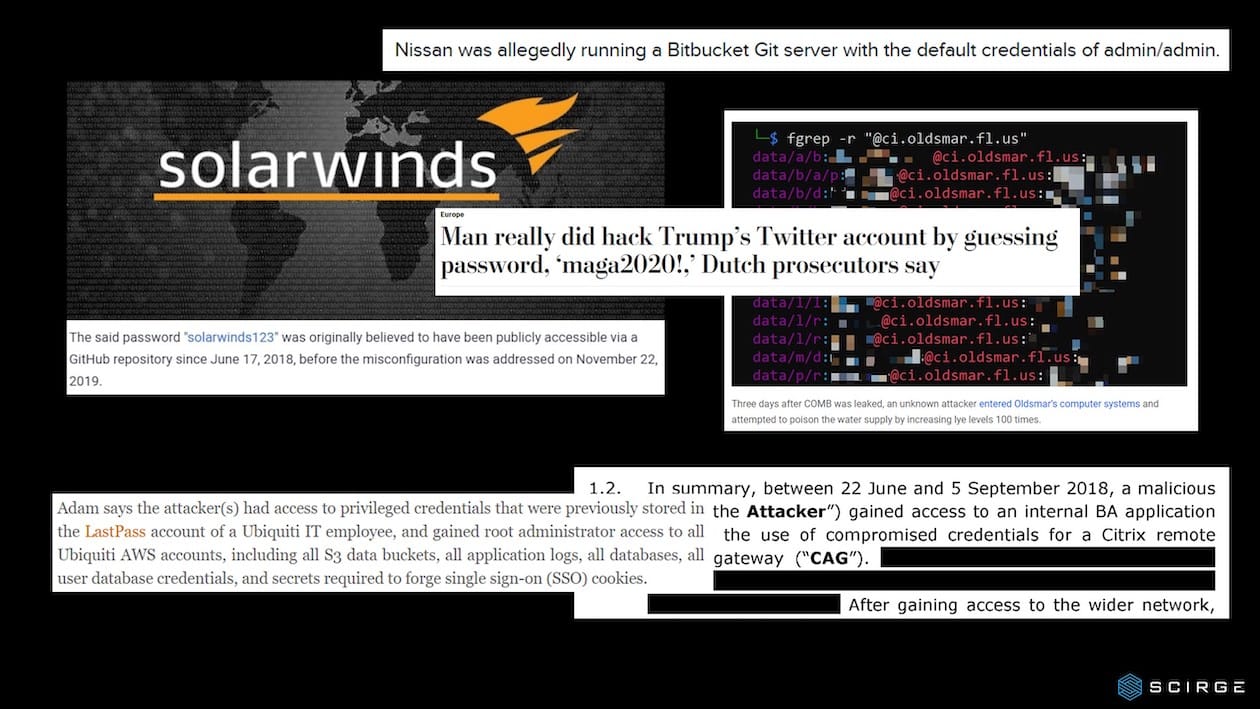
Password strength requirements have been around since the early 2000’s. Although t...

Account takeover (ATO) describes a scenario where user accounts and password integ...

Credential stuffing is the automated injection of usernames and passwords – usuall...

Due to the global pandemic, most of our lives and livelihoods have shifted online....

Secure browsing is often defined by crucial requirements like protecting one’s pri...

Post-breach investigation reports like those from IBM and Verizon agree that for t...

In recent years, businesses have begun to adopt a cloud-first approach with increa...