The Password Security Conundrum
Password strength requirements have been around since the early 2000’s. Although they are one of the rare guidelines outwardly regretted by their authors, their spirit lives on in many forms of regulation and express requirements today. Even industry experts can’t seem to agree on the outdated nature of password complexity rules, some contending that regular password rotation may also be counterproductive. Amidst this confusion, modern requirements still haven’t been synchronized across regulatory guidelines, which often feature conflicting or explicitly opposing recommendations.
For example, regular password changes are still required by PCI DSS v3.2.1:
“8.2.4.a For a sample of system components, inspect system configuration settings to verify that user password/passphrase parameters are set to require users to change passwords at least once every 90 days.”
NIST, the U.S. National Institution for Standards, insists that password complexity rules and contextual filters should be applied while recommending organizations to check against compromised password lists:
- Passwords obtained from previous breach corpuses
- Dictionary words.
- Repetitive or sequential characters (e.g. ‘aaaaaa’, ‘1234abcd’).
- Context-specific words, such as the name of the service, the username, and derivatives thereof.
However, in stark contrast to PCI, NIST also prohibits other complexity rules and periodic password changes unless clear indicators of compromise emerge:
“Verifiers SHOULD NOT impose other composition rules (e.g., requiring mixtures of different character types or prohibiting consecutively repeated characters) for memorized secrets.
Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.”
ISO 27001 also requires the use of “quality passwords” while deeming regular password changes “as necessary” without declaring an exact timeframe. This can be quite confusing for users and security administrators alike.
A more recent guideline from BSI, the German Federal Office for Information Security, is the 2021 IT Grundschutz Compendium (Basic IT Protecion Compendium). This article places a very clear ban on purely time-based password change policies:
“ORP.4.A23 Regulation for password-processing applications and IT systems [IT operations] (B)
IT systems or applications SHOULD ONLY prompt you to change your password with a valid reason. Purely timed changes SHOULD be avoided.”
This implements an arguably more modern approach; it does not force users into regular password changes, as this will eventually lead to cross-using credentials across systems. Frequent changes also influence users to reuse very similar phrases or elementary variations of those phrases, such as changing a few characters or numbers within a password. Once such a password gets compromised, it narrows down the password space significantly, rendering brute-force attempts very effective by using a dictionary of passwords generated from the same phrases.
BSI also adds several very important requirements that are thought to comply with AD accounts, third party services, and SaaS. In this case, password reuse is impossible to detect without tailormade tools.
“ORP.4.A8 [Passwords] MUST NOT be used more than once. For every IT system or every application, a single appropriate password can be used.
Passwords that are easy to guess or in popular password lists MUST NOT be used.”
The UK’s NCSC (National Cyber Security Center) also takes a modern approach that is similar to BSI with their recommendations:
*“Regular password changing harms rather than improves security. Many systems will force users to change their password at regular intervals, typically every 30, 60 or 90 days. This imposes burdens on the user and there are costs associated with recovering accounts.” *
One tick for the “no rotation” party.
“Passwords need to be protected within your system, even if the information on the protected system is relatively unimportant. Reuse of passwords means that an attacker can use this information to attempt to access more important accounts, where further damage can be done.”
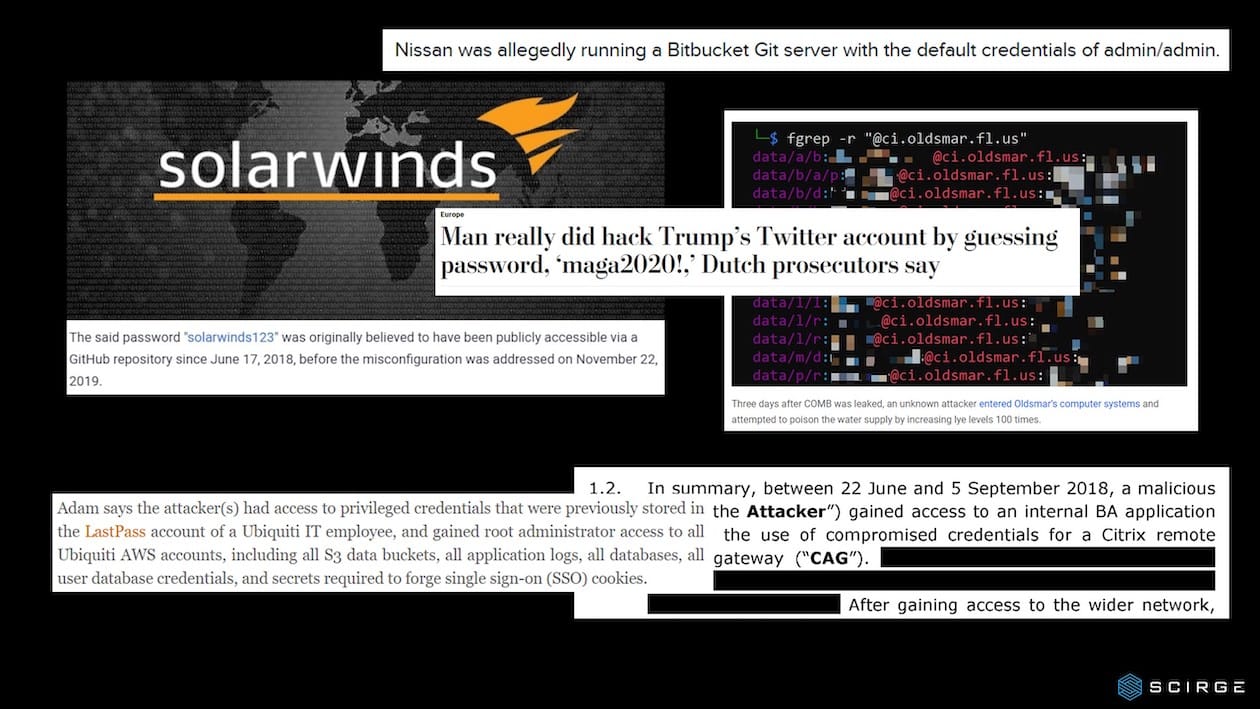
We welcome the above notion as the first clear-cut indication from regulators. Shadow IT accounts beyond managed SaaS services should be monitored, as password reuse has risen to become the number one attack vector according to multiple research studies.
BSI goes on to say:
*“If alternatives are not possible, and there remains a strong business need for shared access to an account or device, then access to the password should be monitored and continually reviewed to manage the risk:
- the password should only be shared within the smallest possible group of known and trusted users
- the password should not be exposed to users who do not have permission to access it
- if someone is no longer allowed access, the password should be changed.”
Amazing! It seems like the more recent a regulation is, a greater emphasis is placed on protecting every password from being reused or shared. This requires IT security teams to put effort into comparing passwords with common password and breached databases.
Conclusion
Although password complexity and rotation policies are highly debated, it is clear that regulators understand the risk of credential leaks, account sharing, and weak credentials. Newer guidelines are shifting the focus from “what we should required from our users” to “the responsibility falls into the hands of security departments” to take control of accounts. This is a momentous shift away from the archaic practice of blaming employees for large-scale compromise as a fallout from weak credential usage.
There is no doubt that employee awareness efforts play a key role in improving password hygiene. However, research has proven that it’s best to combine personal password hygiene with the right tools to check for reused, weak, or contextual passwords, account sharing, breached passwords, reused AD passwords, and more. Expanding upon the above, it is clear that the view should shift from local and managed applications to all employee-created Shadow IT accounts—as long as passwords are still around!
About Scirge
Scirge provides a unique approach to unveil and gain control over unmanaged third-party web accounts. Scirge tracks the websites employees use corporate email addresses to register on and log in to. Having a central dashboard of discovered accounts helps to reduce the risk of credential-related threats such as password reuse or account takeover (ATO). Scirge gives a level of control over SaaS usage to overcome Shadow IT. It also helps to ensure that your company complies with GDPR, CCPA, and other audit requirements.