Are Password Managers Broken?
Very recent breaches at LastPass and Norton LifeLock have stirred up the debate about whether using enterprise password managers is safe, or which one is better in general. Most businesses don’t rely on a single firewall for network protection or a single endpoint security product for the detection of threats. So why should we assume that a single layer of protection, using a single product is sufficient for keeping business accounts secure?
We should note that password managers alone are insufficient in the first place for multiple reasons:
-
They are opt-in for employees, so they probably never provide full coverage for all accounts.
-
They do not block password reuse or sharing (the latter may even be a feature for better or worse).
-
They allow you to store weak passwords.
-
They also generally have a master password, that can not be stored in their vaults, so the most crucial account of all will likely be human-created. By its nature, those are much easier to crack than what the length and complexity would indicate.
That being said, password managers are not broken, we just need to understand their limitations and add other layers of protection just like we do for so many other things.
For example in the case of LastPass, lists of emails and URLs were unencrypted in the stolen vaults. The fact that a business is using a certain SaaS tool or website alone is in itself very sensitive, as hackers may utilize this information for targeted phishing, credential stuffing, and other methods. PayPal was recently hit exactly this way, affecting 35,000 user accounts.
Web-based accounts in most cases are a big part of Shadow IT, so operations and security have a difficult time creating awareness or other controls around them. So how to create an additional layer of protection without adding even more overhead or friction to employee workflows?
Create visibility for the organization.
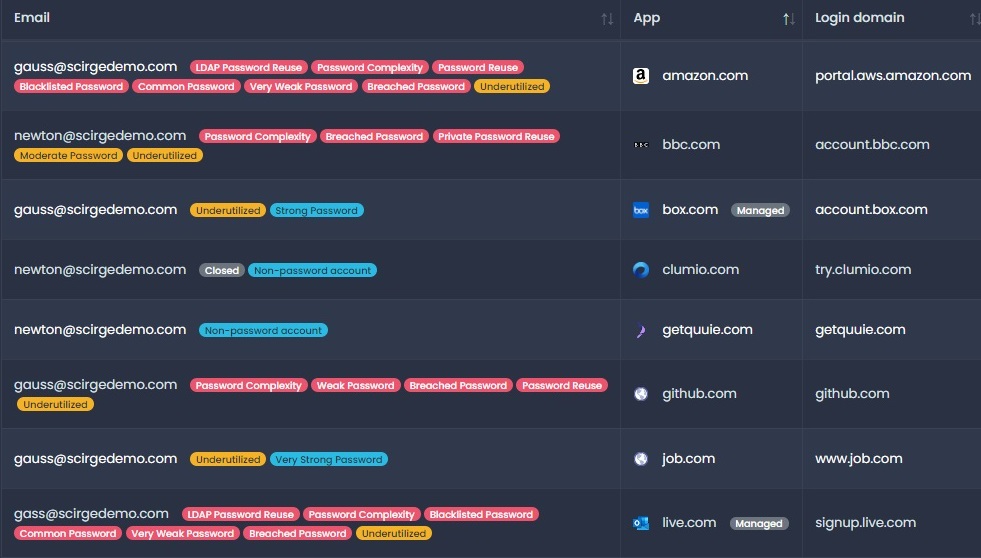
The issue with online accounts is that they are created individually, without the need or possibility for security departments to assert control. This means that applications are sprawling the organization in form of Shadow IT. These apps are accessed via potentially weak Shadow ID passwords and are often involving critical business processes, PII, or confidential data. To assess which applications are accessed by who, what accounts are created, and what password strengths are in place is essential to assess potential risks. Does this remind you of something? Yes, NIST’s Zero Trust guidelines also require you to inventory your digital assets, and the same goes for Data Controllers and Processors by GDPR, and industry best practices curated by CIS as well.
In case a password manager has been rolled out, it also makes sense to discover if all accounts are stored within them, whether they are strong enough, and whether unwanted sharing or suspicious usage pops up.
Enforce policies
Using internal or service accounts for third-party registrations, and having legacy accounts of ex-employees or abandoned services should be dreaded because attackers will always find the weakest links. The same goes for the reused password, especially if they are the same as AD/LDAP accounts, as this is still the top attack vector for obvious reasons. Once someone leaves the organization, or an application is no longer supported, accounts should be removed and access revoked to close backdoors.
Educate continuously
Employees are not security experts. They will not start to utilize state-of-the-art recommendations just because they saw a video or attended a training session. Understanding which departments or employees have higher privileges and risks, and nudging them with appropriate messages should be a slow but continuous effort to improve the overall hygiene of the business. Digital suppliers, and Shadow IT pose the largest threat because no logs, integrations, or advanced monitoring capability is available for security operations to monitor their status. Remember AMD? They are a tech company and have used ridiculous passwords that led to almost a half Terabyte of data stolen. Elevate your employees by supporting them throughout their online journey, every single day.
About Scirge
Scirge provides a unique approach to unveil and gain control over unmanaged third-party web accounts. Scirge tracks the websites employees use corporate email addresses to register on and log in to. Having a central dashboard of discovered accounts helps to reduce the risk of credential-related threats such as password reuse or account takeover (ATO). Scirge gives a level of control over SaaS usage to overcome Shadow IT. It also helps to ensure that your company complies with GDPR, CCPA, and other audit requirements.