Oh, Behave! –Lessons About Attitudes and Behaviors Towards Cybersecurity
The recently released report by the National Cybersecurity Alliance on the perceptions and actions of people around cybersecurity has many lessons for professionals. Mainly, that attitudes and behaviors are quite disconnected in some cases, and that the key to improvement may not lie where we thought it may. Let’s take a look at a few of their findings.
Who is responsible?
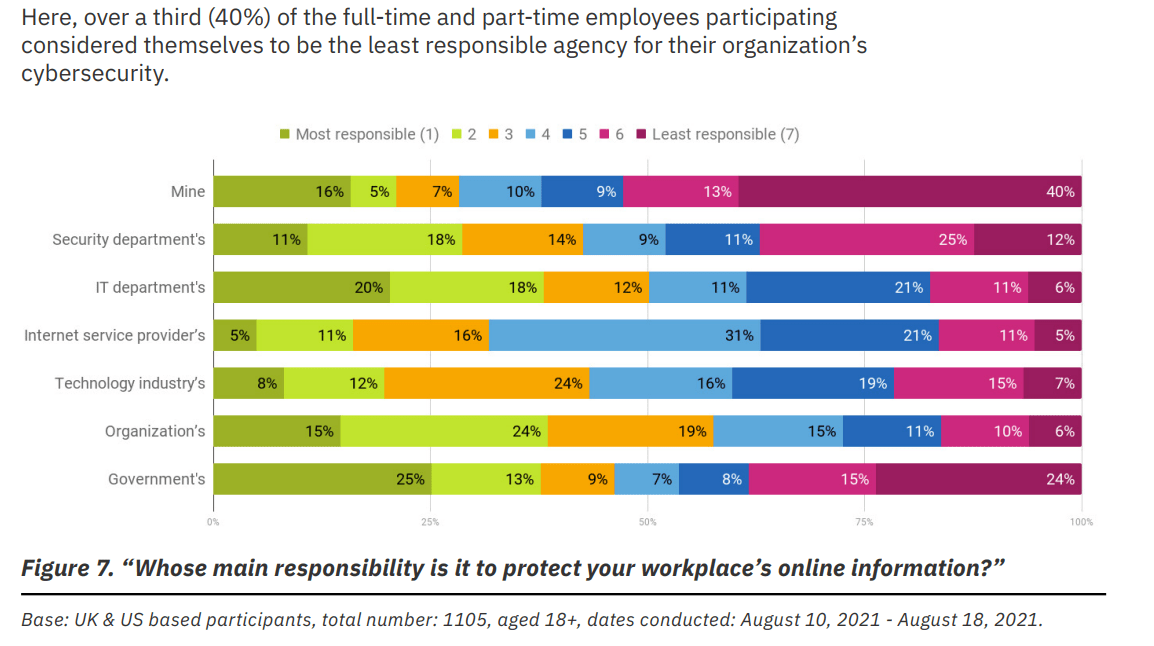
It shouldn’t come as a surprise, that people focus their efforts on their specific job roles, and think that they „simply don’t see themselves as responsible for looking after their workplace’s sensitive information.” It is however a surprise, that only slightly more people -about 51%- feel the same way about protecting their personal sensitive data. This shows an overall lack of care for the security of private or proprietary data and raises a significant alarm for the need for better education around the why’s of cybersecurity.
Reporting crime
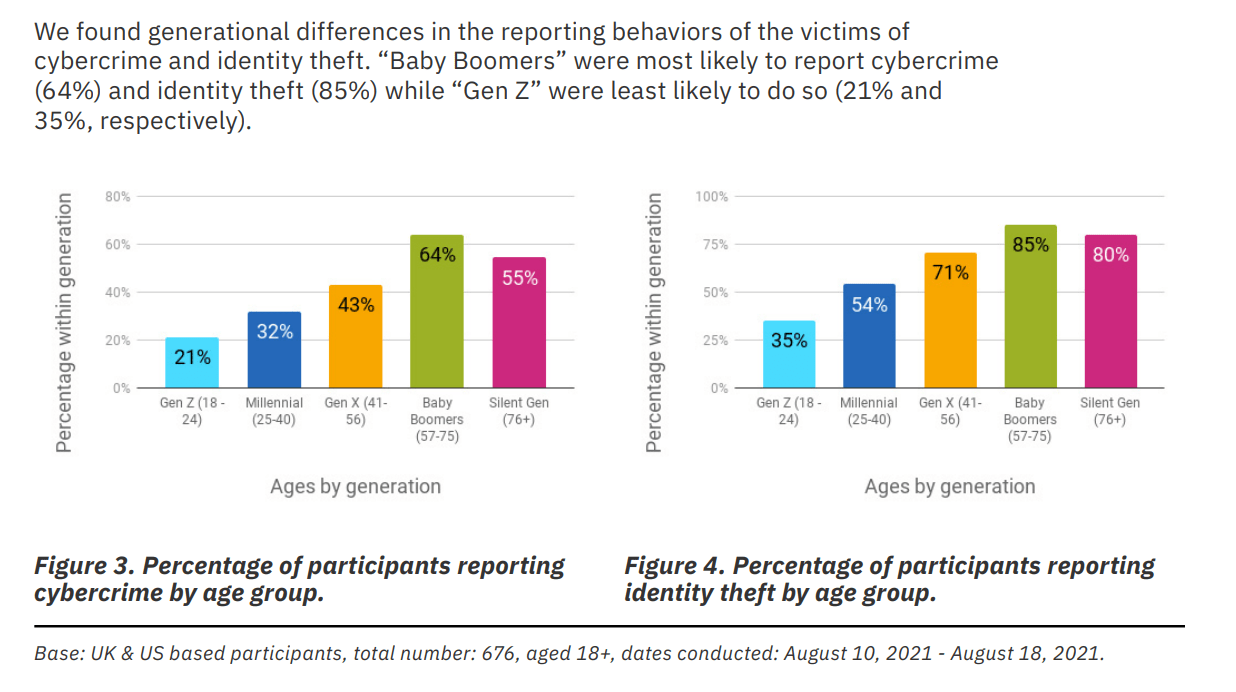
A strong correlation between age and willingness to report crimes is unveiled in the report. A young Gen Z employee is only half as likely to report incidents compared to Gen X. What does this mean for professionals? That training may also have to be aimed better not based on job roles or privileges, but based on age and perhaps other factors as well. Take note though as “61% of the cybercrime victims chose not to report the incident at all.”
Shadow IT in the making
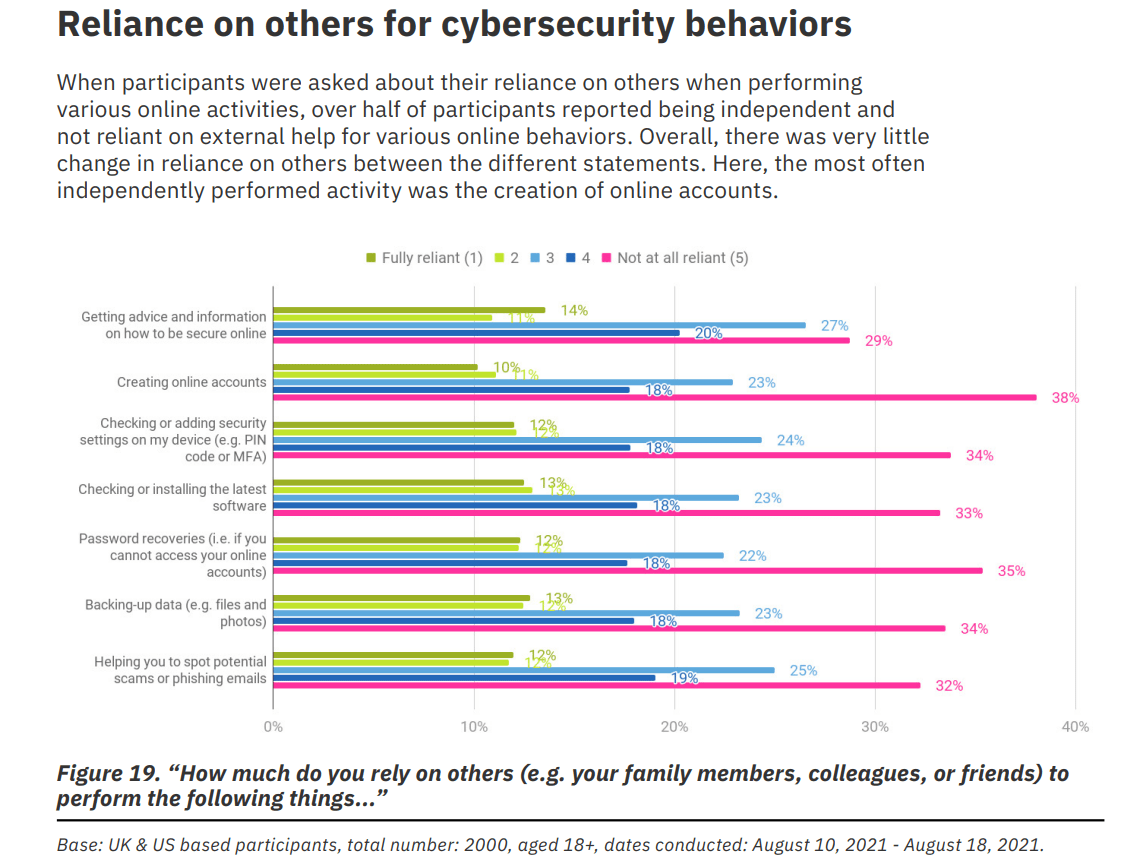
When asked about relying on others for conducting security measures, everyone seems to be mostly independent and confident in their abilities. The highest confidence though is about creating online accounts. Enter your email address, choose a password, isn’t it simple?
Password management
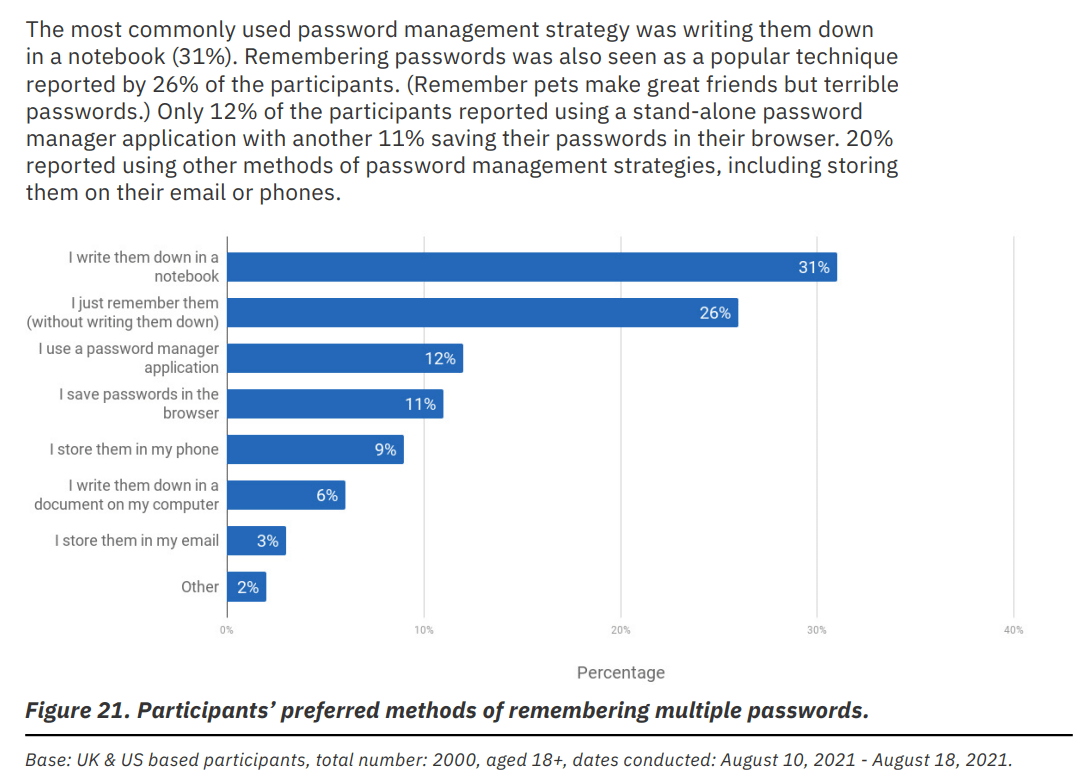
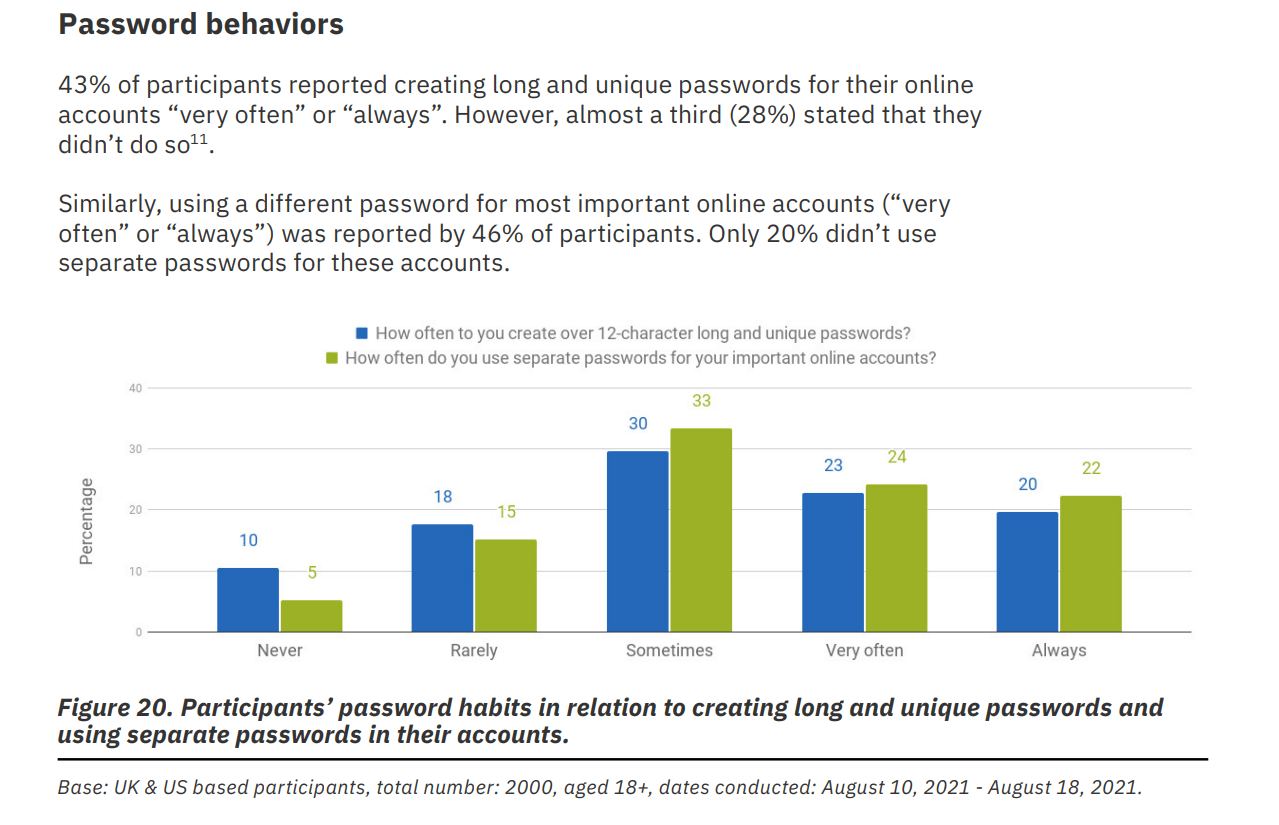
Only 12% of people use dedicated password managers. Almost the same is true for using browsers, which are well known to be extremely vulnerable for storing accounts. The password notebook is the most common method, which can be pretty safe for personal use, but has some concerns when it comes to being on the job. Who can identify which services are being accessed after someone leaves the organization? How will anyone remember their accounts in case the notebook is lost? And how often is the same password being used? As it turns out, over 50% of respondees admit to barely creating strong passwords, and reusing the same ones over and over again.
MFA is not a miracle cure unless taken
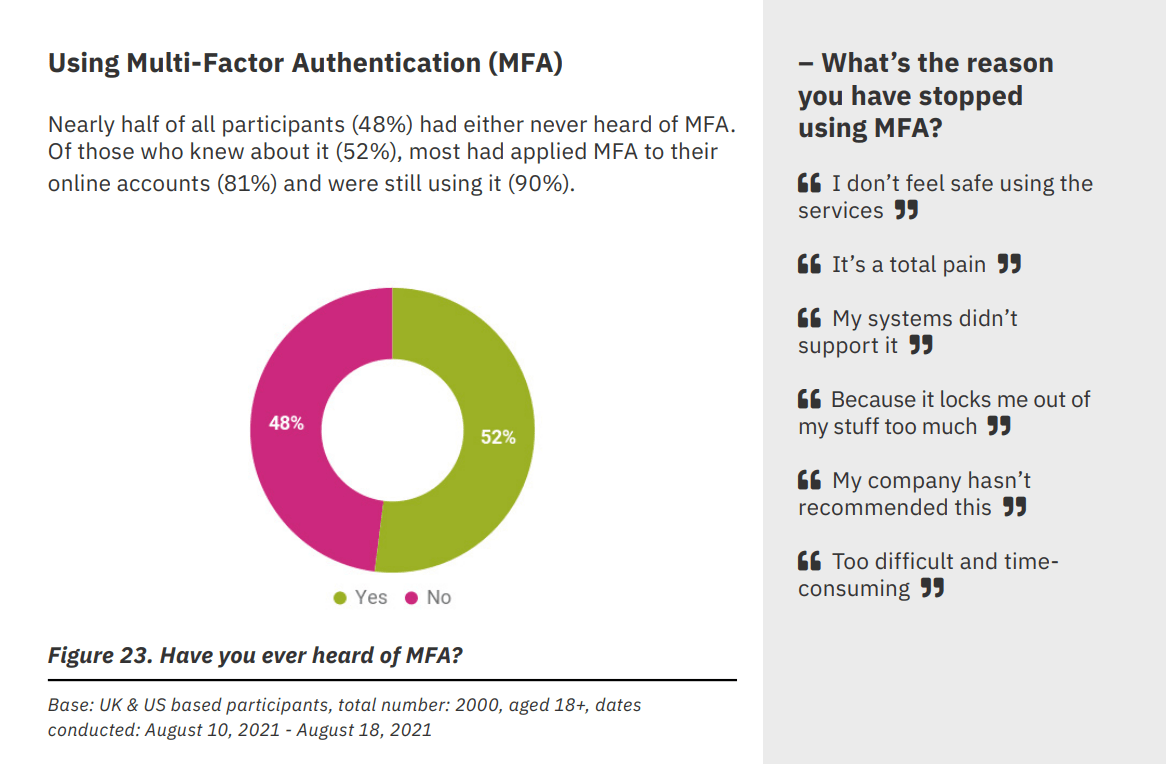
MFA is certainly a key concept of securing accounts and creating security across the board. Overall, 48% of people have never heard of it. This may be an underrepresentation of enterprise workers, as people that did are using it in a very high proportion. This is a strong indicator that education around how and why to use MFA needs to come in pair with deployments. This is especially true for third-party or Shadow IT applications where no enforcement or visibility is available, and MFA is an opt-in service just like password managers.
Training effectiveness
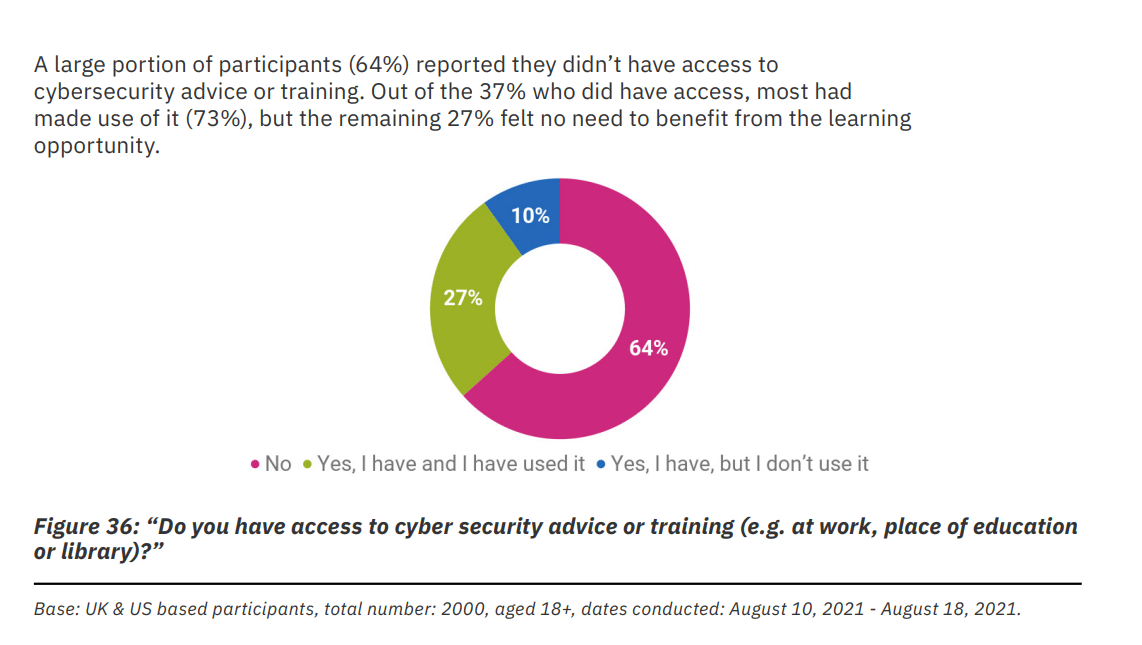
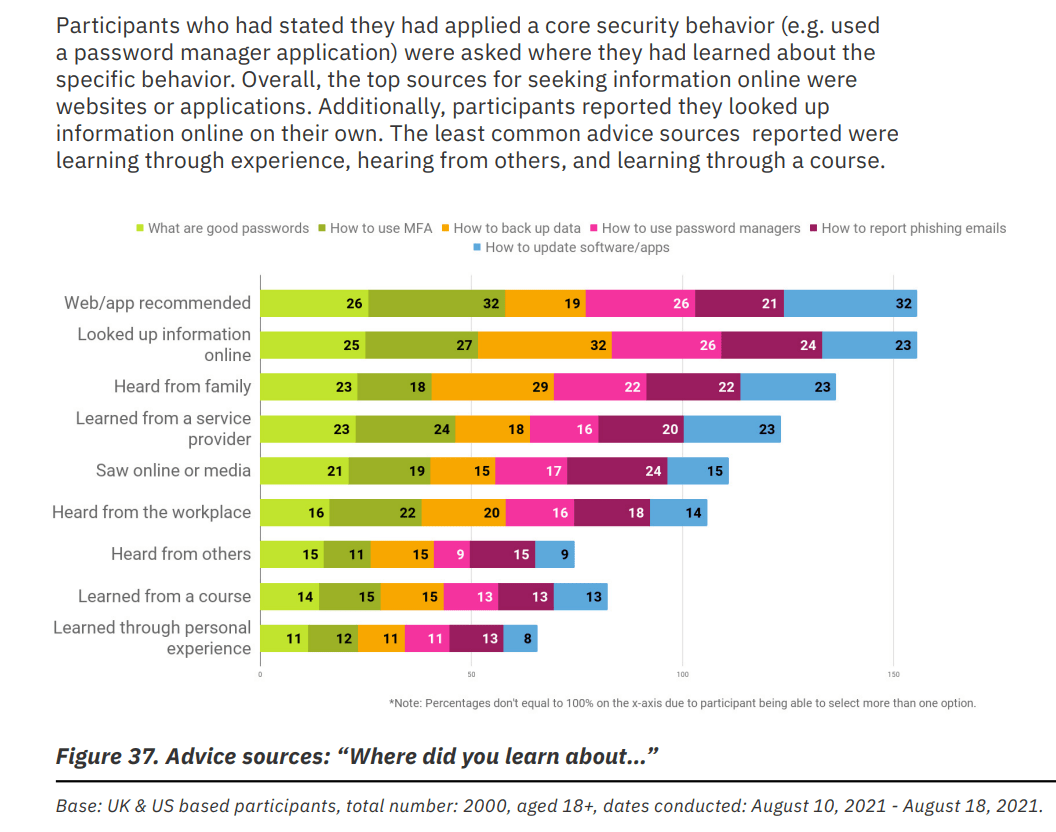
The fact that most people have not received any training may not come as a surprise overall, but 73% of those who did are making use of it. This may be interpreted as good or bad. But more interestingly, people that show adoption of security methods such as using a password manager have mainly learned them directly from websites, applications, or from their online research, plus their family.
This raises the question of what channels and tools should we deliver our training across, as learning on courses or at the workplace doesn’t even come near in its overall effectiveness.
The research data reinforced the importance of awareness and engagement efforts to drive good security behaviors through public campaigns. It’s also clear from the data that websites and other online sources are important sources of information, as stated by those who had reported the adoption of good security behaviors.
Summary
If you have mixed feelings about this report, you are not alone. We have created two ways to summarize the above, trying to interpret both the good and the bad sides of the story.
The gloomy version
People don’t think they are responsible for security, rarely report incidents, and are confident in creating their accounts. often using insecure or reused passwords, rarely using secure password managers or MFA. They are less likely to learn from corporate training than from random websites or unprofessional advice from family.”
The optimistic version
People that have undergone some sort of training are mostly following best practices. Once they get familiarized with MFA concepts, they are very likely to continue using them and are highly independent in taking security measures or learning from sources that they believe can benefit them. As they get older and more experienced, they also take more responsibility in reporting incidents.
Our conclusion
Learning from the above, we should consider adjusting our awareness efforts with a few nudges that may make all the difference, here is our take on that:
- Adopt training methods that emphasize individual responsibility and contribution to the overall security of our organizations, give employees a reason to care.
- Target your audience. One-size-fits-all approach doesn’t cut it when it comes to education (dah). Differentiate based on job roles, but also based on what they are already doing or know. And maybe use different languages or channels to make sure everyone is mobilized.
- Provide relevant and timely content. People are willing to learn when they believe it is right for them. Identify those moments rather than sending them to scheduled courses with overwhelming content.
- Measure stuff. If one thing’s for sure, people are different, so are organizations. Your specific challenges may lie completely elsewhere than what can be derived from such a survey. Measure the usage of MFA, password managers, and anything else that can give you raw data, to tell you where to improve.
About Scirge
Scirge provides a unique approach to unveil and gain control over unmanaged third-party web accounts. Scirge tracks the websites employees use corporate email addresses to register on and log in to. Having a central dashboard of discovered accounts helps to reduce the risk of credential-related threats such as password reuse or account takeover (ATO). Scirge gives a level of control over SaaS usage to overcome Shadow IT. It also helps to ensure that your company complies with GDPR, CCPA, and other audit requirements.