Reporting on Shadow IT – Scirge Version 3.4
One of the hardest things to do when it comes to security is to measure ROI. Test labs pump out a great deal of research regarding the effectiveness of security products but how to decide if a certain tool is performing well in our specific implementation? In the case of shadow IT discovery and account protection, Scirge is in a unique position, because the intel and indicators we provide are extremely exact and measurable. And with our latest release, we are now able to present our data clearly and concisely. Scirge 3.4 introduces a full-blown reporting capability that allows all stakeholders and departments to get relevant details about shadow IT applications, accounts, risks, and results of automated processes and educational efforts.
Built-in reports are designed to reflect on our use cases so that experts and leadership can pinpoint relevant metrics. Let’s see some examples.
Shadow IT Discovery
The primary goal of detecting employee-created accounts is to reveal which applications are used for business purposes, without the consent or knowledge of various IT and security stakeholders. Shadow IT reports allow technical CxOs to understand what kind of services are emerging across departments that may hold sensitive PII or financial data, and where does potential technical debt accumulate through third-party suppliers. In the case of larger organizations, underutilized, abandoned, or overlapping services may even reveal excessive subscriptions and license costs.
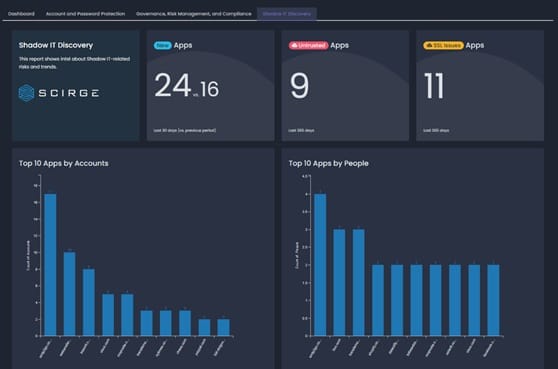
Built-in reports reveal usage-based toplists and risky apps as well. For security audits, third-party applications can be scrutinized for their reliability:
- Isn’t there a better service in place where employees could use SSO?
- Do we have a sanctioned app for the same purpose that employees do not know about? Should we roll out one?
- Is it a reliable service at all?
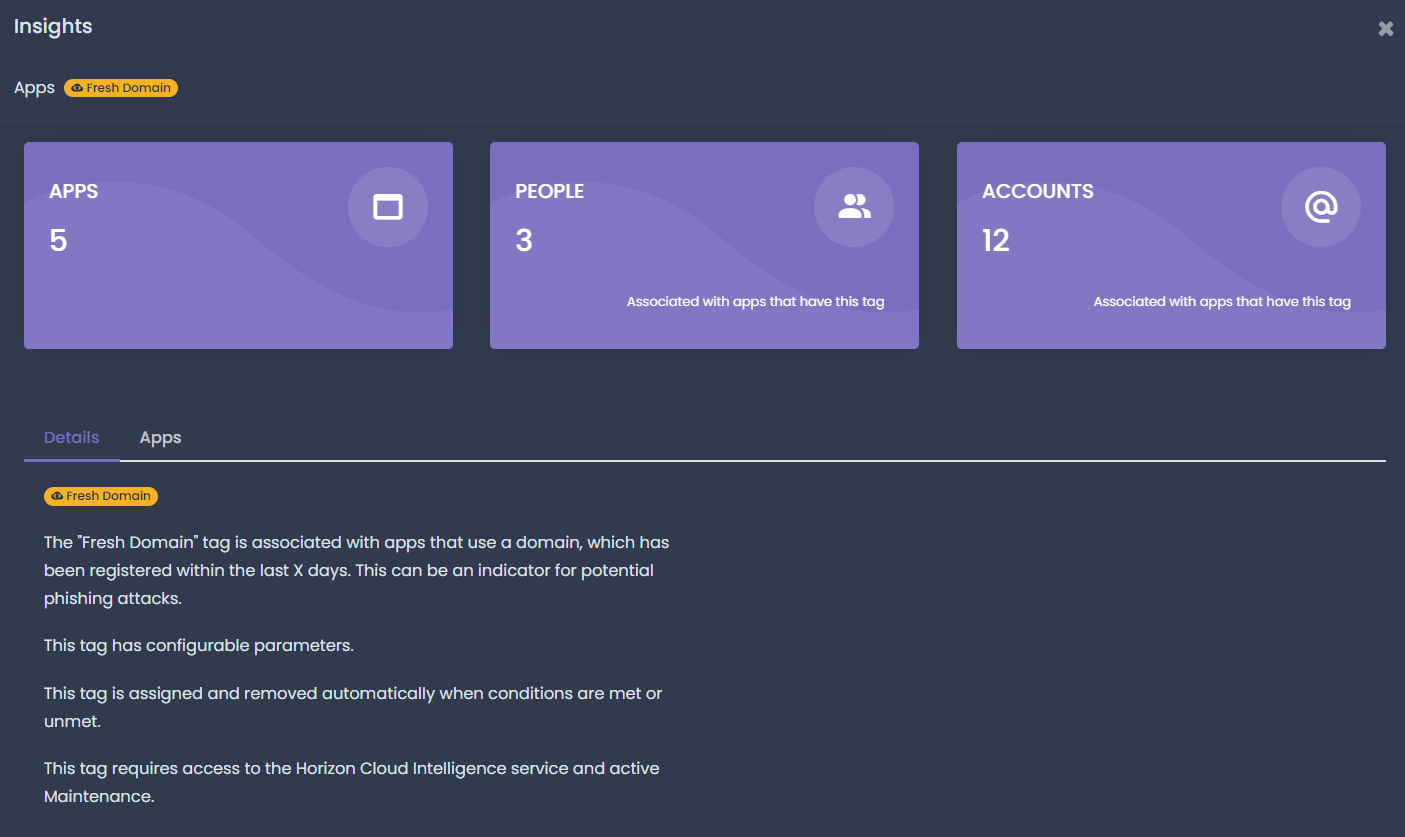 |
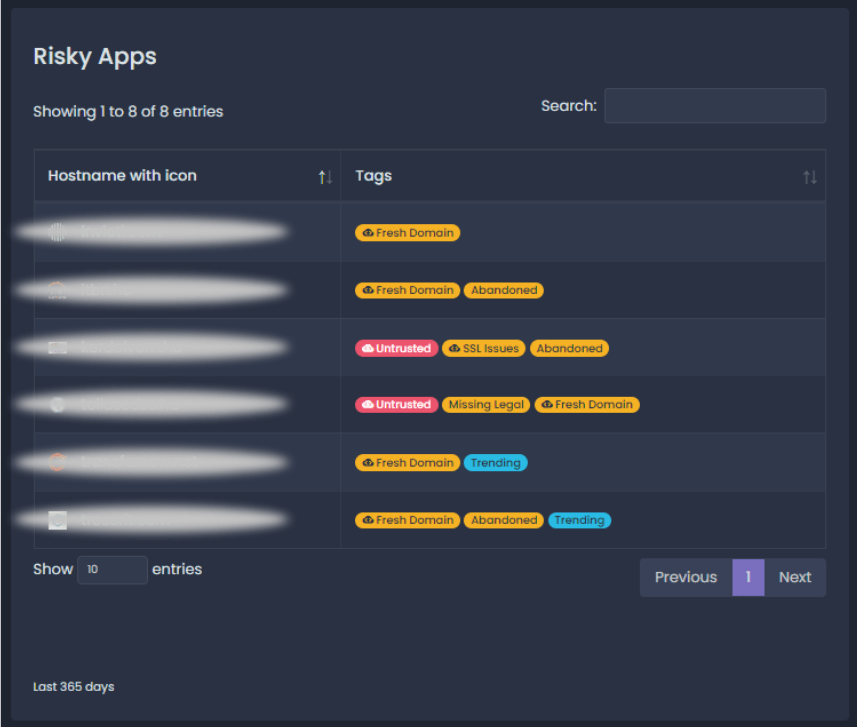 |
IT security departments should also be able to drill down into risky apps. Websites that have recent domain registrations, low trust scores, or issues with their SSL certificates may be malicious or simply unreliable to hold business data, or even a business credential. Reports allow experts to drill down into each individual app or risk indicator, or even create custom views and use-cases specific to their organization or industry. No wonder, that CIS recommends keeping these inventories as well.
Account and Password Protection
The toughest security challenge of third-party accounts, however, are the emails and passwords that are used across hundreds of websites, pretty much by all employees. Whenever they join or even just try a new app, service, or simple website, they must create an account. And with a few exceptions of sanctioned, SSO-based logins, they can only rely on either a personal account or their business email to log in. By monitoring and collecting account details from the browsers, inventories of Shadow IDs (Shadow IT accounts) emerge, with tons of indicators around potentially weak or even breached passwords.
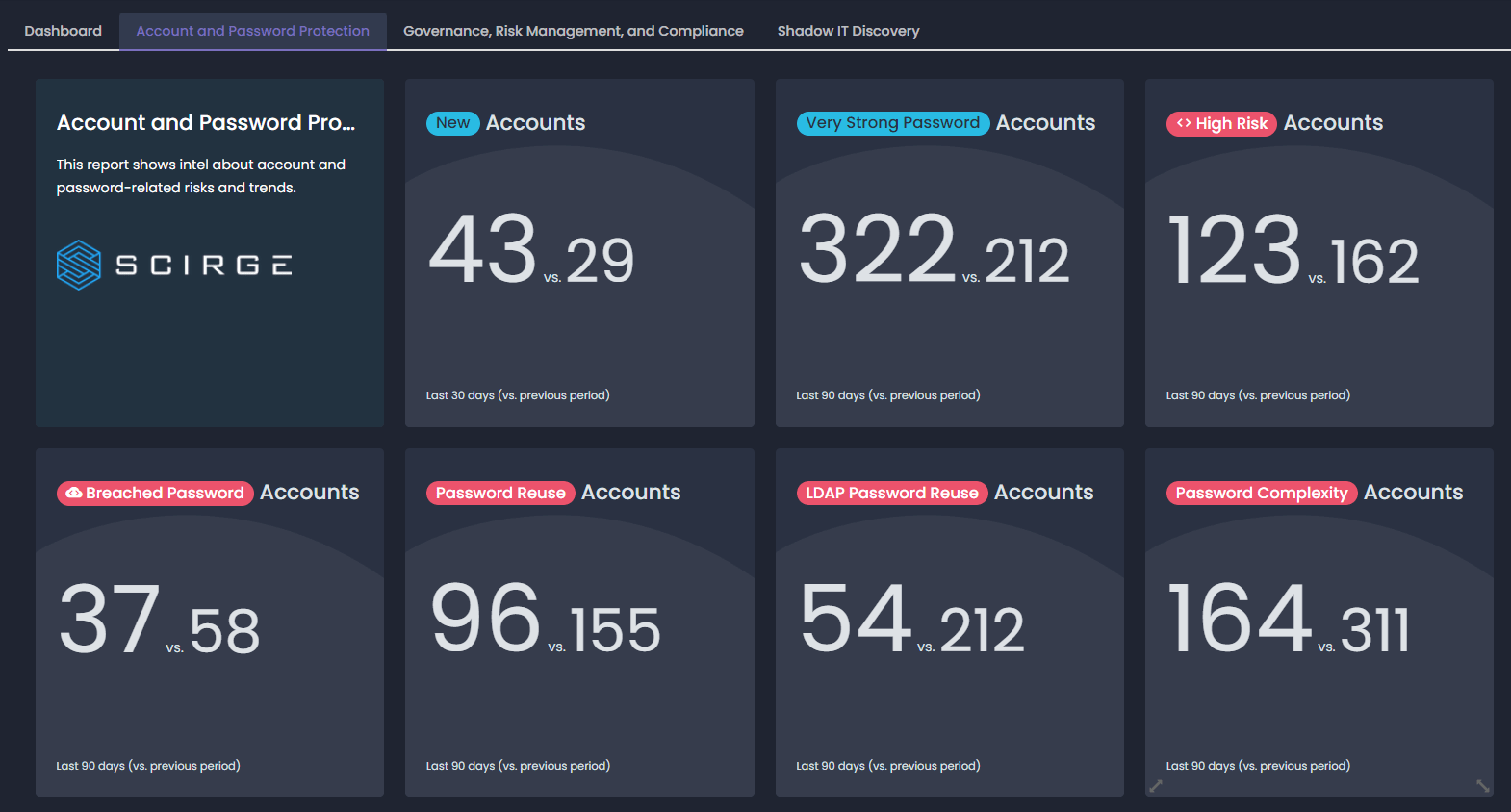
These reports make show the data about weak or reused passwords in black and white. If our training and awareness campaigns are effective, employees should be using fewer weak passwords. Instead, they will generate unique and strong ones with their password manager or using reliable complex passphrases that we have educated them about (haven’t we?). They will not reuse their AD passwords on third-party sites, and will not share sensitive and personal account details even with co-workers unless it’s unavoidable. Until these efforts are complete, however, attackers will always look for weak passwords as they are one of the simplest ways inside. For an employee that falls victim to a fake login site to phish for their passwords, or a legacy VPN connection, with a vulnerable second factor. Whichever it is, passwords are the number sought-after asset that is being targeted by phishing, website breaches, and malware. Measuring their password hygiene and constantly improving employee behavior when using them, should be one of our priorities.
Governance, Risk Management, and Compliance
Organizations under regulations or self-imposed risk controls should be aware of the legal and business risks associated with unknown applications. Whether it’s a recommendation by NIST or a hard requirement from GDPR, we must be evaluating our suppliers, service providers, and sometimes even risky employees. Supply chain risk, external data processors, and unknown accounts are all part of it. Shadow IT web accounts are one of the least visible parts of our attack surface, as no amount of scanning or log collection will make them appear. Applying the proper controls for risky apps and accounts must start with reporting on their exact metrics and nature, to pinpoint the ones that hold the highest potential risk.
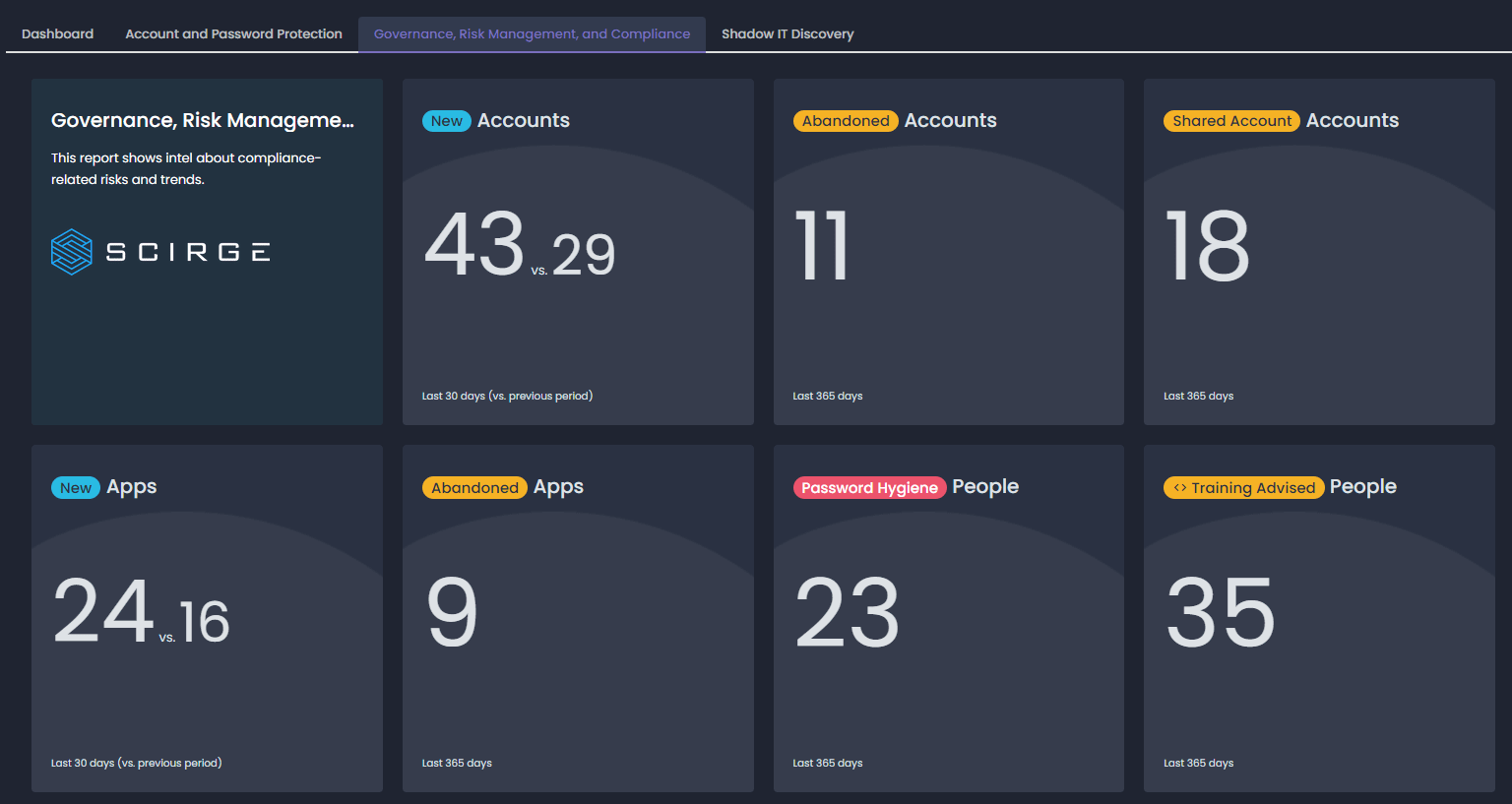
Scirge allows individual customization of each widget and report, sharing anonymized reports and exporting password-protected, scheduled reports to stakeholders. Filtering based on apps, groups of employees, or even certain accounts makes reporting relevant, specific, and actionable.
About Scirge
Scirge provides a unique approach to unveil and gain control over unmanaged third-party web accounts. Scirge tracks the websites employees use corporate email addresses to register on and log in to. Having a central dashboard of discovered accounts helps to reduce the risk of credential-related threats such as password reuse or account takeover (ATO). Scirge gives a level of control over SaaS usage to overcome Shadow IT. It also helps to ensure that your company complies with GDPR, CCPA, and other audit requirements.