Scirge 2.5 Release and Beyond
In order to understand your Cloud footprint, it’s crucial to collect information from endpoints about your employees’ business-related credential and account usage across the web. Scirge is not only able to achieve this with centrally-managed policies, but also adds intelligence and automatic metadata enrichment to uncover cloud consumption trends and password hygiene issues.
With version 2.5, we are extending these capabilities to pinpoint risky users and potential misconduct, revealing potential fraud and segregation of duty conflicts. These new features also enable you to discover if your key employees may be at risk of impersonalization or account theft by an insider.
Introducing People Tags
To kick off Scirge 2.5, let’s start with the brand-new Password Hygiene Tag. This tag may be used to inform security officers about which employees are using a relatively high number of weak passwords. First, we need to set the minimum password strength that we would like to meet for all employee accounts. Then, we can set a ratio that will check the password strength tags for all accounts belonging to a user. Let’s say we set it to a Strong Password and 20 percent:

In this example, any user that has over 20% of all of their accounts with weaker than “Strong Password” will have a Password Hygiene Tag associated with them, indicating that they have not reached this password security threshold.
Another simple manual tag that is now available in the People Inventory is the VIP Tag. This identifies high-privilege users, executives, or other key personnel in the organization. This tag may be used in conjunction with other tags to create alerts or filter inventories based on events related to VIP users.
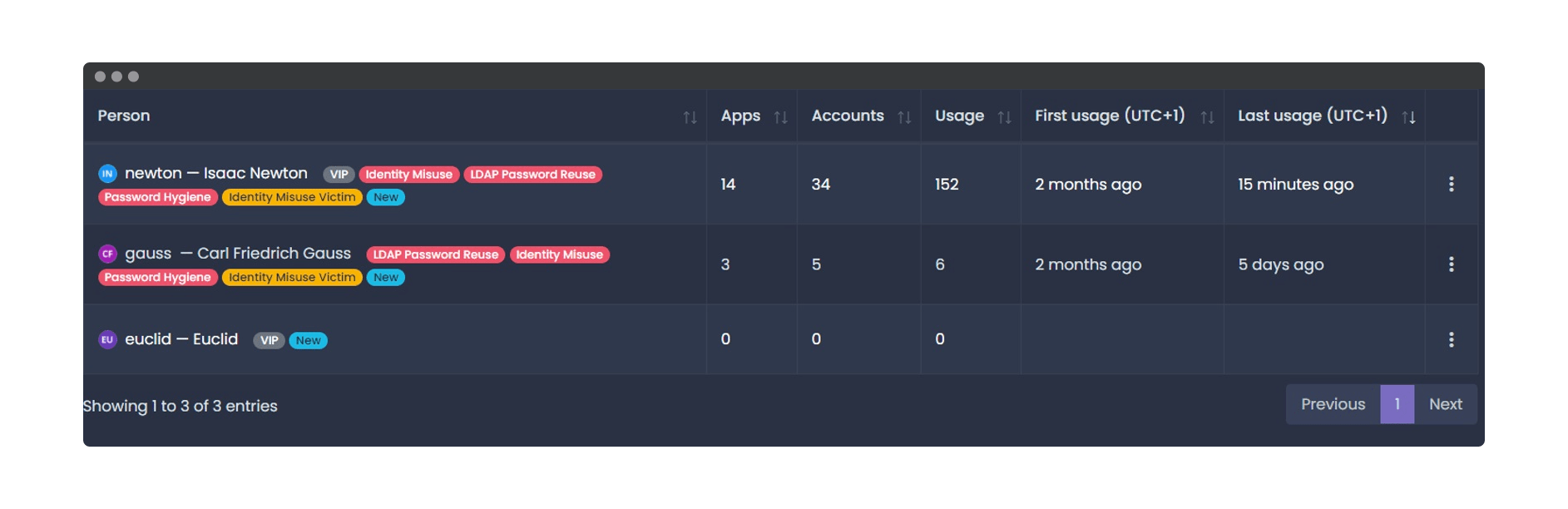
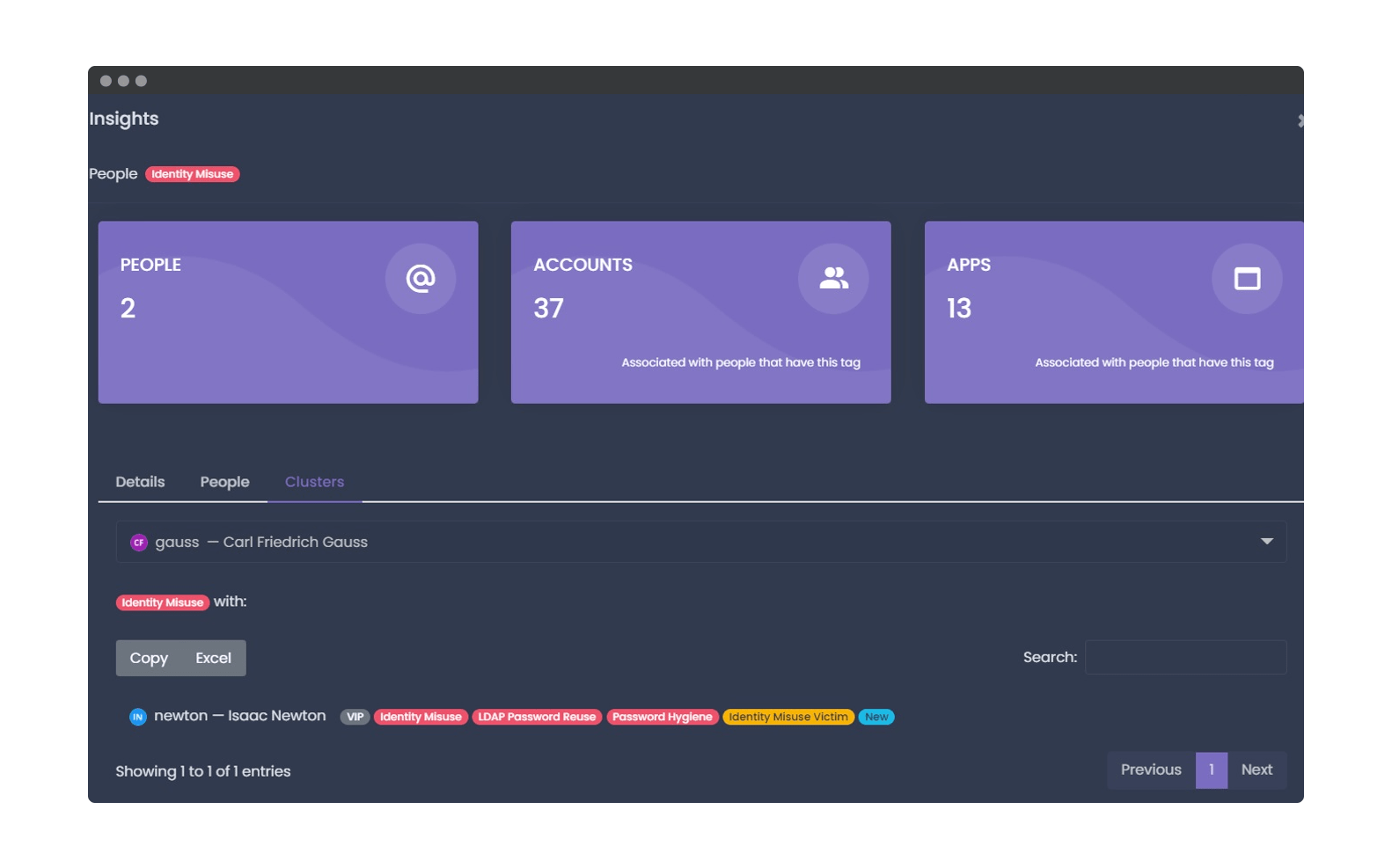
A pair of new tags that we have introduced for employees are Identity Misuse and Identity Misuse Victim. These tags are associated with individuals who utilize another user’s primary email address, indicating that they are potentially impersonating someone else within the organization. The Identity Misuse Tag is associated with the user who is using someone else’s address, while the Identity Misuse Victim Tag is associated with any user whose primary email had been used by someone else.
As usual, clicking on any of these tags will show the Insights popup. This will display the correlation between accounts, clustering which user was impersonated by another.
We’ve also added new tags that will sync the user account status with the Active Directory and mark if a given user account is disabled or deleted. Furthermore, if a person is using an online account where the email address is the primary address of such a user account, it will get flagged with an Inactive LDAP Account Reuse Tag. This makes it easy to detect if people are using accounts that belonged to employees who have already left the organization.
Onboarding Guide
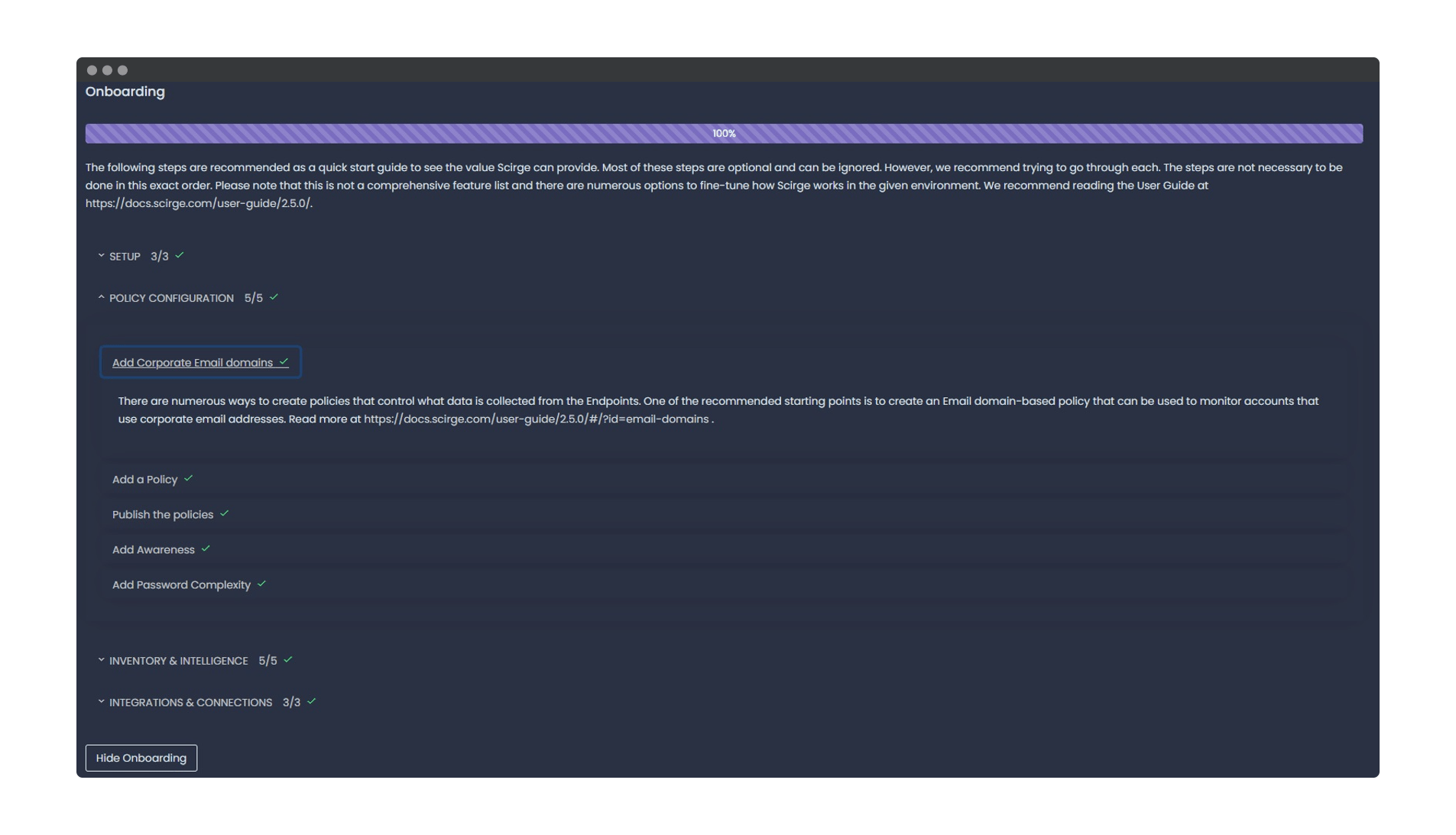
Implementing a new product for the first time is always a challenge. With this in mind, we wanted to ensure that getting through the initial setup goes smoothly without overlooking any important steps. In 2.5, we have introduced the Onboarding Guide available in our Dashboard.
Overall progress is shown based on the individual steps that are divided into four groups. All steps will include a short description and a link to the appropriate segment in the user guide. Once a certain step is completed, such as creating the first policy or awareness rule, it will automatically be marked as done. Of course, this can all be hidden in case you are already experienced, or just have a knack for doing things your own way!
Endpoint Improvements
Our Endpoint Browser Extensions are the soul of Scirge, and as such, we are always looking for ways to improve their security, performance, and usability. With this update, we have added an Endpoint API Key option as an additional security layer, so that only authorized endpoints can reach Scirge management. This can be used in tandem with the authentication and authorization methods already in place.
The biggest and most important feature for endpoints, however, is that you can now set up a custom domain for the central server connection. This will make the implementation options more flexible, and is very useful if the central server needs to be accessible from the Internet.
This feature will enable home office workers and road warriors to keep their endpoints updated with policies and enable them to send back logs. It’s important to note that these employees will still need to connect to the corporate network in order to upgrade the Endpoint Browser Extension to the newer version.
What’s next? Scirge 3.0!
While all of the above combined makes for great improvements, we are not stopping here. We are planning to implement a major update sometime around the end of the first quarter. Here is a sneak peek of what you can expect from our next major version.
Active Directory Password Hygiene
This will leave you in awe. We are extending our password hygiene check for local AD accounts! Did you know that 70% of all local accounts are easily crackable? This means that adversaries attempting to access to your local networks can have a blast gaining privileges in minutes. With our upcoming release, you will never lose sleep over heavy regulatory requirements and weak credentials protecting all of your well-kept secrets.
Scirge Horizon Cloud Intelligence
Soon, we are planning on introducing our proprietary intelligence feed. This will further enrich your inventories with metadata and check for passwords that are already compromised and accessible in the wild.
Getting excited? Please share this article to show you your love! In case you have the urge to give it a try or have any questions, let’s get in touch!
About Scirge
Scirge provides a unique approach to unveil and gain control over unmanaged third-party web accounts. Scirge tracks the websites employees use corporate email addresses to register on and log in to. Having a central dashboard of discovered accounts helps to reduce the risk of credential-related threats such as password reuse or account takeover (ATO). Scirge gives a level of control over SaaS usage to overcome Shadow IT. It also helps to ensure that your company complies with GDPR, CCPA, and other audit requirements.